IT Security Audits- Key Concepts
The IT security audit is a critical part of the organization’s cyber defense strategy, and it must be planned and executed carefully. Cyber risks can come from many sources such as compromised passwords, lost or stolen devices with sensitive data on them, malware in an email attachment or website that compromises your device or network.
Quick Links
It is vital to know what you’re delving into before an IT security audit. The first step in an audit is to understand the key concepts such as what is an IT security audit, how it works, and why do we need them? This article post will answer these questions and more!
What Are IT Security Audits?
An IT security audit is the comprehensive examination of an organization’s information technology (IT) infrastructure and operations to assess the effectiveness of its security controls. The aim of any organization is to have 100% confidence in its cyber defenses, but this is not always possible. This is where IT security audits make an entry!
The goal of an IT security audit is to identify areas where improvements can be made in order to reduce cyber risk. It also provides assurance that the organization’s information assets are adequately protected.
IT security audits are often performed by third-party agencies that specialize in the field. Some of these companies offer both internal and external IT security audit services.
IT security and IT security audits are not the same. IT security is a broad term for all of the organization’s cyber-security controls, while IT security audits go in-depth to assess and discover controls and areas of possible development.
Now that we’ve covered what IT security audits are, let us check out their relevance for companies!
Why Are IT Security Audits Important?
IT security audits are an integral part of the organization’s cyber defense strategy. The number of cyberattacks is on the rise, and businesses are increasingly recognizing the importance of conducting regular IT security audits to protect their data and systems. An audit can help identify vulnerabilities before they are exploited by hackers, and it can also help ensure that your organization meets compliance requirements.
In order to understand why IT security audits are important, we first need to take a look at the different types of cyberattacks that businesses face on a daily basis.
Types of Cyber Attacks:
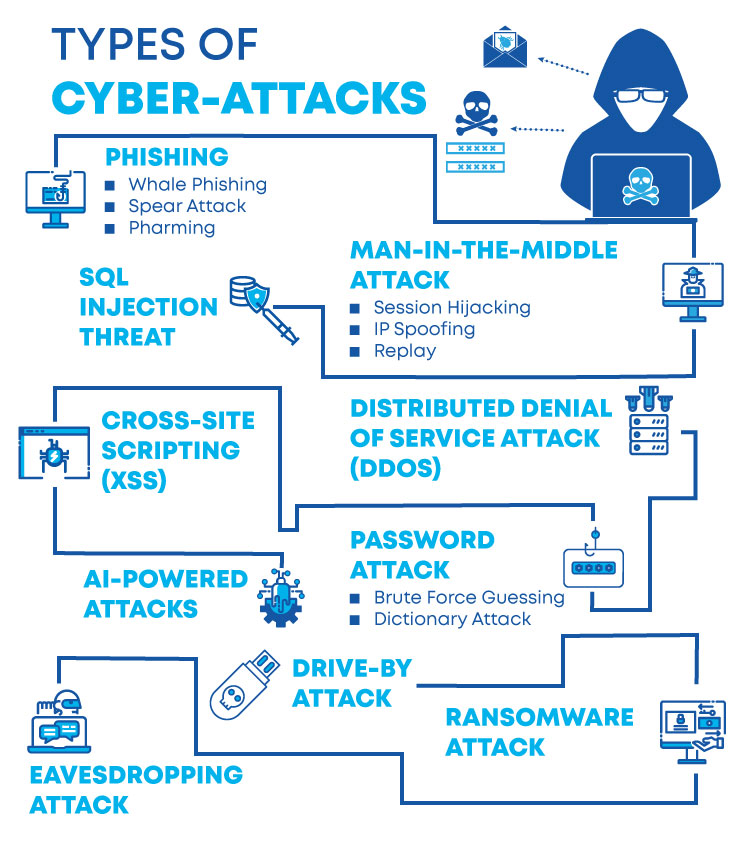
There are many different types of cyberattacks that businesses can fall victim to, but some of the most common ones include:
- Phishing attacks
- Denial of service (DoS) attacks
- Malware and ransomware attacks
It is important to note that not all cyberattacks are large in scale, many can be quite small but still very harmful. Even if you think your business is too small or insignificant for hackers to target, you should still conduct regular IT security audits as a preventative measure. In real-world circumstances, the security in the cloud element is commonly exploited. An insecure AWS instance exposes your whole business and customer data to hackers, and if compromised, it may have serious consequences for your brand’s reputation, consumer trust, and income. As a result, it is also critical to do an AWS Security Audit while there is still time.
How do IT security audit reports help companies?
An IT security audit report provides a detailed summary of the findings from an audit engagement, along with recommendations for improving your cybersecurity posture. The audit will also provide proof that your company is doing its best to protect itself from threats like malware attacks, ransomware, data theft, etc. The report can be used to provide evidence of due diligence in the event of a data breach or other cyber incident, as well as support requests for funding to improve your organization’s cybersecurity defenses.
The main objective of an external IT security audit report is to highlight risks so you can prioritize them based on the potential impact they may have on customers or business operations if not addressed. The information given in the report should be actionable so it can guide management teams through any required changes needed for improving overall cybersecurity posture within a short time frame. It should also encourage executives at every level throughout the organization to implement proactive solutions when dealing with daily routine issues and challenges.
How Does IT Security Audits Work?
How Does It Work? The process of conducting an IT security audit begins with the selection of a target, which could be anything from a specific system or application to the entire network. Once the target is selected, auditors will review relevant documentation such as policies and procedures, configuration settings, and vulnerability reports.
The scope for an IT security audit varies depending on your organization’s needs, but it generally involves a comprehensive review of all aspects related to cyber defense such as password protection, firewalls, network configuration, and encryption policies among others.
The agency conducting the assessment will look at how well each control is implemented and if they’re working effectively to reduce risk exposure. Next, they will test the systems and applications against established baselines or industry best practices using both automated tools and manual analysis. Finally, they will produce a report that includes findings and recommendations.
What Is An IT Security Audit Checklist?
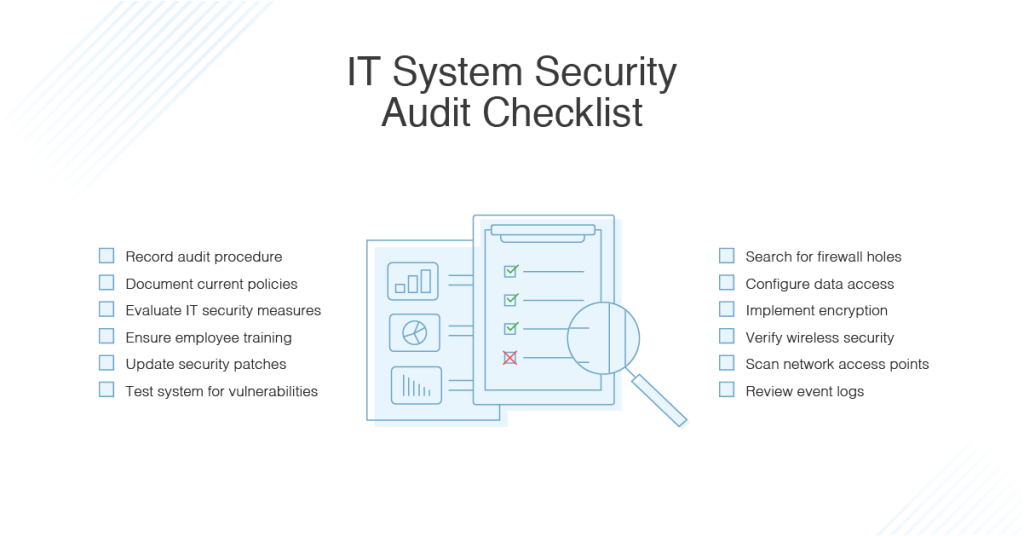
An IT security audit checklist is a comprehensive list of items that need to be checked during an external or internal IT security audit. A typical checklist used during an external or internal IT security audit includes:
- Password management practices
- Security updates
- Firewall configuration and management (internal)
- External firewall security
- Intrusion detection policies, procedures, and tools
- Cybersecurity monitoring tools and technologies used
- Spam filtering practices
- Encryption protocols for sensitive data storage and transmission
- Software patch management procedures and tools
- Mobile device security policies, processes such as Mobile Application Penetration Testing
- Operating Systems such as Windows Server, Unix/Linux based systems
- Data Loss Prevention strategies
- Content Management Controls
- Best practices for employees
How To Prepare For An IT Security Audit?
The first step in preparing your organization to undergo an external or internal IT security audit is proper planning. You will need to identify all the information that will be needed by the agency conducting the assessment such as passwords, network configurations among other things so they can conduct a thorough review of your systems’ cyber defense capabilities. This way you’ll get accurate results with detailed recommendations on how best to improve your defenses against cybersecurity threats.
Now let us take a look at some of the key points that should be considered when preparing for an IT security audit.
- Reviewing your organization’s cybersecurity policies and procedures
- Identifying systems and applications that need to be audited
- Documenting the audit’s scope and requirements
- Ensuring all devices used by employees are configured correctly
- Identifying any gaps or risks associated with your current cybersecurity practices
- Evaluating security awareness training programs for employees
- Online Penetration Testing your systems and applications against established baselines or industry best practices
- Updating system patches and software
- Reviewing firewall configurations
- Implementing intrusion detection strategies
What’s To Be Done After An IT Security Audit?
After the IT security audit is complete, the auditor will compile a report that includes findings and recommendations. The report will help identify any gaps or deficiencies in your organization’s cybersecurity posture and suggest ways to mitigate these risks.
You should also work with the auditor to develop an action plan that will address the issues identified in the report. This plan should be implemented as soon as possible to reduce your risk exposure and protect your organization from potential cyber-attacks.
Conclusion
The article has given you an introduction to IT security audits and all the key concepts that are required for them. It is important that companies invest in this, as they will be able to provide better protection of their data assets. Find the best organization to address your IT security audit needs to help with these matters involving your company’s safety.
Author Bio: Ankit Pahuja is the Marketing Lead & Evangelist at Astra Security. Ever since his adulthood (literally, he was 20 years old), he began finding vulnerabilities in websites & network infrastructures. Starting his professional career as a software engineer at one of the unicorns enables him in bringing “engineering in marketing” to reality. Working actively in the cybersecurity space for more than 2 years makes him the perfect T-shaped marketing professional. Ankit is an avid speaker in the security space and has delivered various talks in top companies, early-age startups, and online events.
Why WooCommerce is the Best Choice for Your Online Store?
WooCommerce stands out as a top option for anyone looking to build an online store. This platform…
0 Comments8 Minutes
How to Use AI-Powered SEO Tools for WordPress eCommerce
SEO is a critical factor in the success of any e-commerce WordPress store. As competition…
0 Comments11 Minutes
Why Short-Form Videos Are the Future of Content Marketing
Your Instagram customers spend over 50% of their time watching short-form videos and reels. Rather…
0 Comments12 Minutes
The Role of Digital Marketing in Business Growth
Online marketing touches every aspect of a business, whether it is initiating the idea or for an…
0 Comments3 Minutes
AI Meets Authenticity: Balancing Automation and Human Touch in Content Marketing
Is your brand starting to sound like a robot? In a world where algorithms write faster than any…
0 Comments8 Minutes
Essential Tools for Enhancing Web Design and UX Hosting
Have you ever visited a website that felt slow, clunky, or confusing? A website that is poorly…
0 Comments11 Minutes
How a Mini Cart Transformed My Store’s Shopping Experience
Okay, real talk—running an online store is hard. You think you’ve got everything figured out, you…
0 Comments9 Minutes
Balancing Your Security Initiatives With Industry Compliance Requirements
Managing a business today comes with a number of daily battles that need to be fought. Resources…
0 Comments11 Minutes








