Cyber attacks are worse than ever. Here’s how to protect your business.
What if I told you that 60% of small-to-medium sized businesses close up their doors after a data breach?
Quick Links
Or that cybercrime soared by a massive 600% during the pandemic?
And if you’re in an organization of any kind of size, you’ve probably experienced receiving suspicious phishing emails or strange log-in attempts to your back-end. That’s just par for the course nowadays.
So, what can you actually do about it?
The obvious answer is to tighten up security – but that’s also a vague and frankly unusable answer. Where do you start?
The fact of the matter is that many attacks happen because most businesses have a lot of different frontiers of security: firewalls, antivirus, malware scanners, and DDOS prevention mechanics to mention a few.
Add to that compliance efforts, physical security, data management and monitoring.
A mind-boggling puzzle. A puzzle that leaves behind significant gaps and overlaps. And a puzzle that means that incident responses can take hours or days of continuous work.
Luckily, there are tools out there that aggregate it all. And add a layer of business and operational analytics on top of it.
Enter SIEM.
What is SIEM?
SIEM is an acronym for Security Information and Event Management. It corresponds to a suite of tools that combine previously separate security tools. In short, it’s a tool that gathers and aggregates information about security and events within an IT environment, analyzes it and gives valuable insights to your security team.
In the olden days, you might’ve had separate solutions for each of the following:
- Log management: Simple gathering and storing of log messages and audits
- Security information management (SIM): Storage, analysis and reporting of that log data
- Security event management (SEM): Monitoring and flags in real time of security events
Sometimes this would follow as functions of other tools such as your antivirus or firewalls. The sharp reader will now have noticed that SIEM is a combination of SIM and SEM. The term was invented at Gartner back in 2005.
Essentially, SIEM solutions give a centralized overview of the entire IT security infrastructure and any events happening within it. SIEM as a service can offer a solution and a single point of truth to refer to.The point of course is to provide cybersecurity professionals insights into the IT environment of an organization.
How does it work?
In simple terms, SIEM works by gathering, aggregating and analyzing events and log data from several different sources or end-points. That can be software such as the mentioned antivirus, anti malware or firewall applications. But it’s also physical entities such as Internet of Things-hardware, printers and the computers your coworkers use.
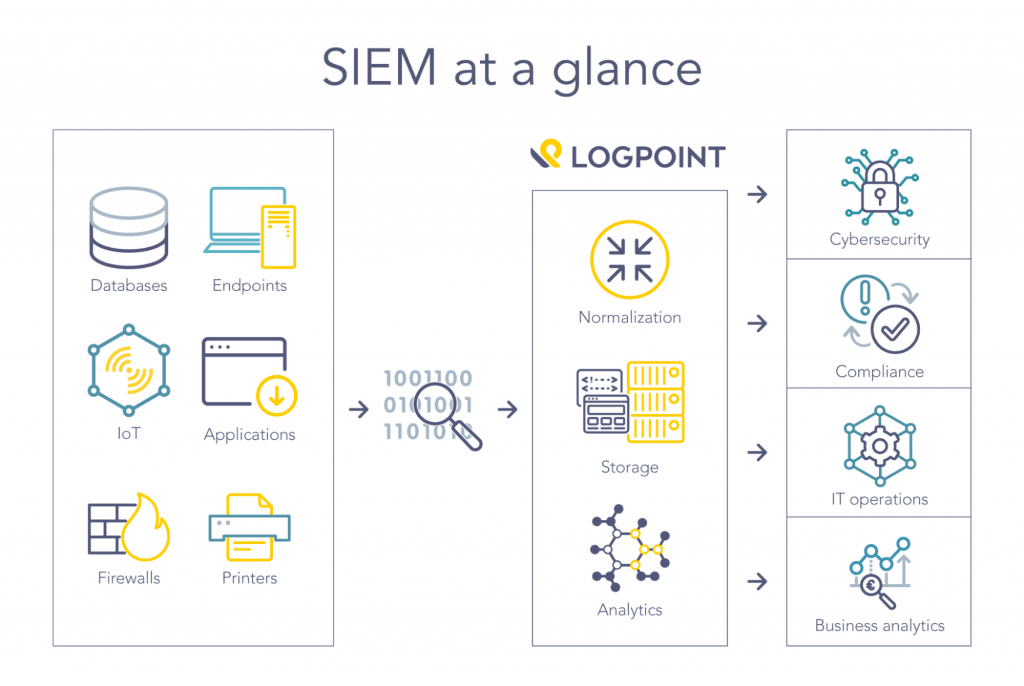
Source: Logpoint – What is SIEM?
After gathering and aggregating this data, it is normalized, stored and provided in real-time to the user. The SIEM solution will then analyze and identify threats, suspicious behaviour and potential issues by comparing to a set of rules.
As an example, someone trying to log in 10 times in an hour is probably normal behaviour. Someone (or more likely, something) trying a thousand times in the same time period is suspicious. Well, unless your coworkers match a specific intersection of forgetfulness and fast typing. This is something a trained eye would identify manually, but that requires a very specific monitoring that there is not time for for most IT security professionals.
The end-user is then supplied with real-time alerts, dashboards and reports that can help prevent breaches and solve them if they ever happen.
What are the benefits of SIEM?
Let’s reiterate the stakes. According to Willis Towers Watson who surveyed 467 firms, enterprises lost $4.7 million annually due to cyberattacks. And 10 of the surveyed firms lost more than $10 million.
I think that by now it is self-explanatory why cybersecurity is important. But why should you also add another layer of analytics on top of that?
The short answer is that no matter your security efforts, no fortress is unbreachable. And with so many endpoints in the modern organization it only takes a moment of carelessness from a coworker before it all comes crumbling down.
So you need a holistic and comprehensive overview of what is going on in your IT realm.
The modern benefits of SIEM
With hybrid workplaces and employees using multiple devices to access critical and sensitive data – and with most organizations collecting more of that data than ever before – it has never been easier or more profitable for cyberattackers to breach your defenses.
And since a lot of you have been in the IT game since before 2005, I think it is due to re-establish what SIEM means in 2021. Because the definition has changed, and the usage has as well.
3 big benefits of a modern SIEM analytics solution
- Data is collected and organized in real time
As stated, enterprises manage more data than ever. And from more sources than ever. To manage all that security and event data effectively, you need something that is able to obtain and handle an increasing amount of data. And modern SIEM solutions do not just handle it well, they also grow smarter by doing it by way of sophisticated algorithms.
- You don’t just need data, you need context
With modern cyberattacks, it’s not just a question of breaching security. It’s a case of breaching people. Social engineering makes up a large part of all cyberattack attempts. It works by tricking or coercing your coworkers into threatening their places of work. This is why most modern SIEM solutions add a layer of machine learning that helps identify suspicious or aberrant user behaviour.
- Improving response time on fewer resources
By automating monitoring tasks, SIEM software means that your cybersecurity professionals get the necessary insights and clarity much faster. Not only that, it frees up valuable time and resources to work on more strategic efforts. In a cynical business view, it could also mean less security staffing requirements. It’s probably self-evident, but when you have a breach you want responses to happen as fast as possible and to be as effective as possible. SIEM software gives you all that in a single interface.
Not just security
However, I realise that getting approval and buy-in for more cybersecurity efforts isn’t always straightforward. The good news is that SIEM provides avenues to not just tighten up your security game, but also in providing business intelligence and compliance monitoring.
Since SIEM’s are built around flexible integrations and being able to connect to a diverse array of endpoints, a lot of them also go above and beyond IT.
Compliance and GDPR-monitoring
With the advent of GDPR, businesses are under more scrutiny than ever. A key point that SIEM can help monitor is the unlawful processing, loss or destruction of sensitive data.
- Static rules and intelligent algorithms help identify misuse of data
- Tracking unusual or unlawful access to data warehouses
- Compliant and sophisticated logging helps backtrack and store the necessary data for any audits
Business intelligence
It’s not just IT security applications that generate a ton of data. A modern, digital organization also employs HR software, ERP systems, payroll processing and a lot of other endpoints that generate data. All of this data can be used to make intelligent business decisions. Or it can be lost to the murky depths of an interface that only one business unit accesses – and never fulfill its potential.
- Turn data into useful information within one report or dashboard
- Centralize the aggregation of data into a secure solution.
- Identify bad configuration of data pathways and storing to optimize future business processes
No, it’s not what SIEM was invented for. But as luck would have it, it’s something it is also really good at.
Conclusion: Is it time for SIEM?
We’ve established some fundamentals here. What SIEM is, what it can be used for and what it means in a modern business context.
It means saving time and headaches for your already-overworked security staff. It means faster and more efficient responses to security threats.
But of course, it’s a tool that only works on top of an already established security layer. So if it’s your first foray into ensuring better security for your business, it’s not the right step. But if you’ve got the basics down, it’s probably the right time to start making it more intelligent and work for you.
And with cyberattacks on the rise, it has never been more prudent to establish more automated and sophisticated workflows to better ensure that your organization stays safe, compliant and risk-free.
Essential Tools for Enhancing Web Design and UX Hosting
Have you ever visited a website that felt slow, clunky, or confusing? A website that is poorly…
0 Comments11 Minutes
How a Mini Cart Transformed My Store’s Shopping Experience
Okay, real talk—running an online store is hard. You think you’ve got everything figured out, you…
0 Comments9 Minutes
Balancing Your Security Initiatives With Industry Compliance Requirements
Managing a business today comes with a number of daily battles that need to be fought. Resources…
0 Comments11 Minutes
Best plugins to enhance the customer shopping experience
Customer experience is a key part of every online store. A good experience helps customers find…
0 Comments7 Minutes
AI Content Generating Tools: Is It A Collaboration or Competition For Content Creators?
Artificial Intelligence (AI) has created waves in content creation in business verticals. From…
0 Comments13 Minutes
How to boost user engagement and conversion in WooCommerce?
One thing that is not changing today or in the coming future is the impact user engagement has on…
0 Comments9 Minutes
10 Proven Digital Marketing Strategies to Skyrocket Your ROI in 2025
Why do some companies have a more robust online presence than others? Marketers know very well…
0 Comments12 Minutes
Why Is Woocommerce Suitable For Small Businesses?
Are you finding yourself more confused than usual when choosing your online business’s platform?…
0 Comments8 Minutes








